漏洞概要
关注数(24)
关注此漏洞
漏洞标题:
siteserver最新版3.6.4 sql inject 第十蛋
>
漏洞详情
披露状态:
2013-11-26: 细节已通知厂商并且等待厂商处理中
2013-11-27: 厂商已经确认,细节仅向厂商公开
2013-11-30: 细节向第三方安全合作伙伴开放
2014-01-21: 细节向核心白帽子及相关领域专家公开
2014-01-31: 细节向普通白帽子公开
2014-02-10: 细节向实习白帽子公开
2014-02-24: 细节向公众公开
简要描述:
siteserver 最新版3.6.4 存在注入, 第12个注入
详细说明:
第11个注入存在/siteserver/cms/console_logSite.aspx
用.NET Reflector 反编译SiteServer.CMS.dll这个文件
查看代码如下:
上面几个参数进入下面
几个Request.QueryString['xxx']都是可注入点
漏洞证明:
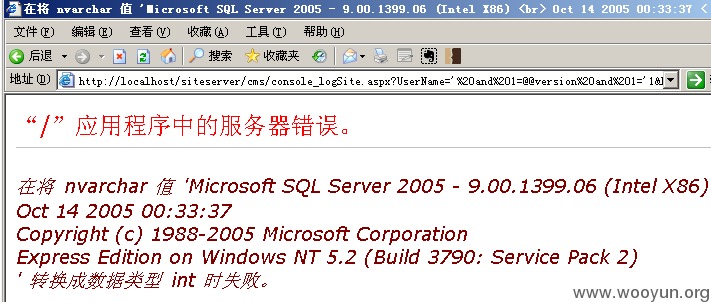
官网
修复方案:
版权声明:转载请注明来源 小新@乌云
>
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2013-11-27 09:31
厂商回复:
感谢小新的工作,尽快修正产品
最新状态:
暂无


