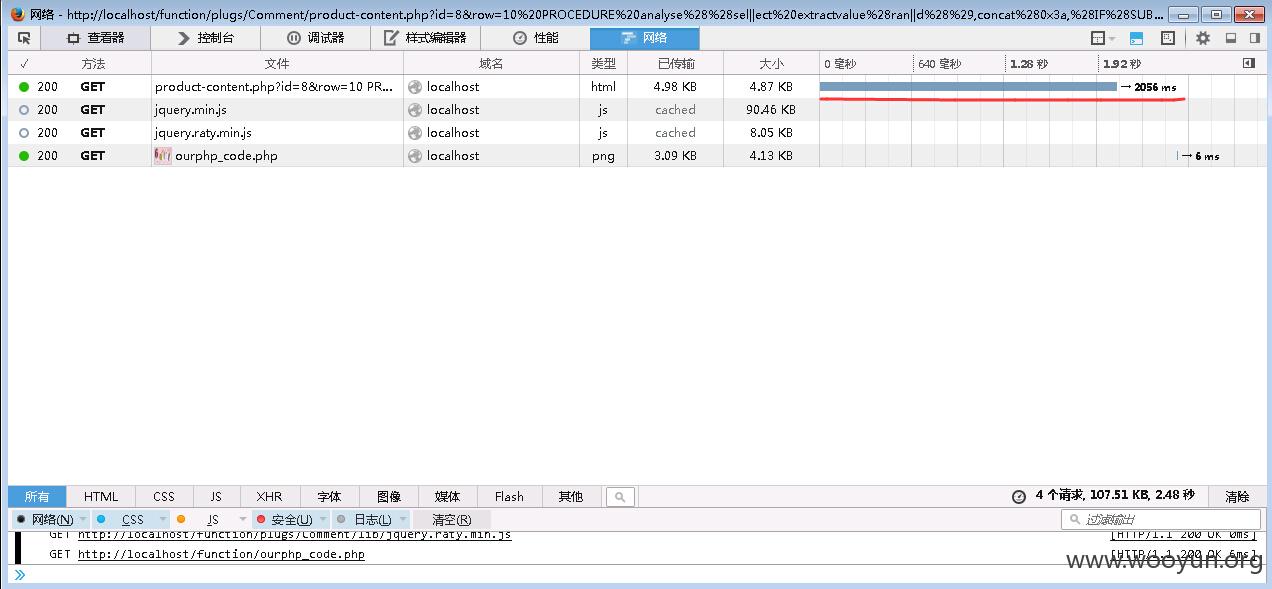
漏洞文件:/function/plugs/Comment/product-content.php
$OP_Class = isset($_GET['id'])?$_GET['id']:"0";
$sql="select * from `ourphp_comment` where OP_Class = ".intval($OP_Class)." && OP_Type = '".dowith_sql($OP_Type)."' order by time desc LIMIT 0,".dowith_sql($OP_Row);
function dowith_sql($ourphpstr){
$ourphpstr = str_ireplace("&&","",$ourphpstr);