漏洞概要 关注数(24) 关注此漏洞
缺陷编号:
漏洞标题:
看我直连高顿www主站数据库(28库/两百万用户数据含密码)
相关厂商:
漏洞作者:
提交时间:
2016-02-01 17:51
修复时间:
2016-03-14 15:10
公开时间:
2016-03-14 15:10
漏洞类型:
重要敏感信息泄露
危害等级:
高
自评Rank:
20
漏洞状态:
未联系到厂商或者厂商积极忽略
漏洞来源:
http://www.wooyun.org,如有疑问或需要帮助请联系
[email protected]
Tags标签:
分享漏洞:
>
漏洞详情
披露状态:
2016-02-01: 积极联系厂商并且等待厂商认领中,细节不对外公开
2016-03-14: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
RT 安全无小事
详细说明:
#1 github泄露:
用户名:root
密码:2Ls56VwEK2wUuYDV
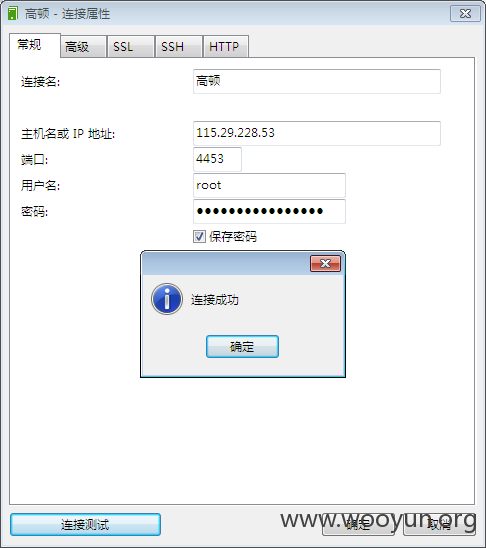
IP地址:115.29.228.53 端口:4453
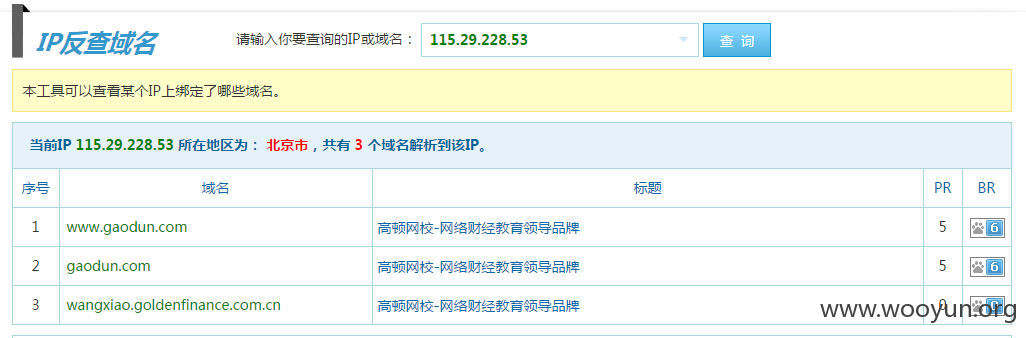
#2 IP反查
#3 连接成功
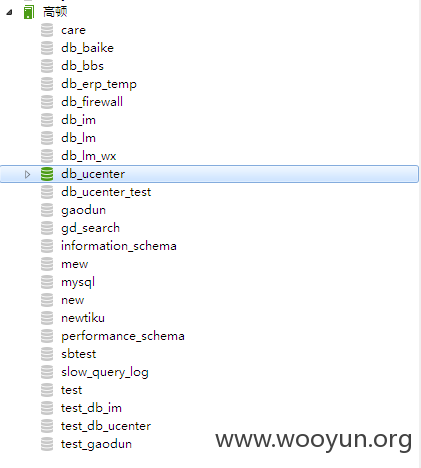
#4 28个库
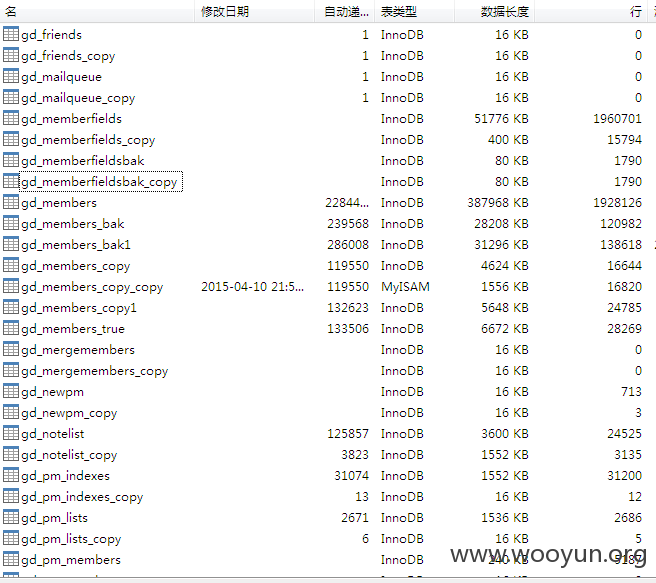
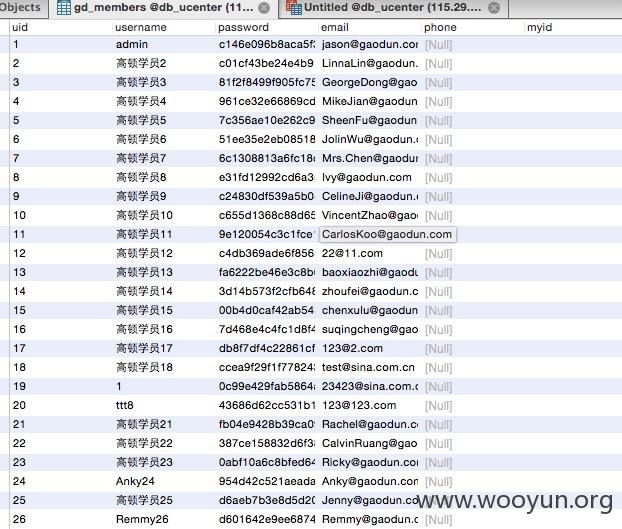
#5 192万用户
#6 root权限不再深入
漏洞证明:
#1 github泄露:
用户名:root
密码:2Ls56VwEK2wUuYDV
IP地址:115.29.228.53 端口:4453
#2 IP反查
#3 连接成功
#4 28个库
#5 192万用户
select count(*) from `gd_members`
1999559
#6 root权限不再深入
修复方案:
#1 内部自查
#2 穷孩子买不起网课,求送~
版权声明:转载请注明来源 JutaZ@乌云
>
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝
漏洞Rank:15 (WooYun评价)